- What is UFONet?
It is a toolkit designed to launch DDoS and DoS attacks.
- What is a DDoS attack?
A Distributed Denial of Service (DDoS) attack is an attempt to make an online service
unavailable by overwhelming it (for example, with traffic...) from multiple sources.
- What is a DoS attack?
A Denial of Service (DoS) attack is an attempt to make an online service
unavailable by overwhelming it (for example, with traffic...) from a single source.
- What is a Botnet?
A Botnet is a collection of computers often referred to as "zombies" that allows an attacker
to control them. It is commonly used to make DDoS attacks.
- What is the philosophy behind UFONet?
"On a samurai sword or even any tool, what matters is who goes to use it and for what,
not who builds it and when..."
- Why can UFONet be more special, than for example, other botnets previously built?
Because UFONet tries not living traces (IPs, etc...) from the origin of the attack. And
of course, because it is free/libre. ;-)
- How does UFONet work technically?
UFONet is a tool designed to launch Layer 7 (APP/HTTP) DDoS attacks, using 'Open Redirect'
vectors, generally located on third-party web applications (a botnet) and other
powerful DoS attacks, some including different OSI model layers, as for example
the TCP/SYN flood attack, which is performed on Layer 3 (Network).
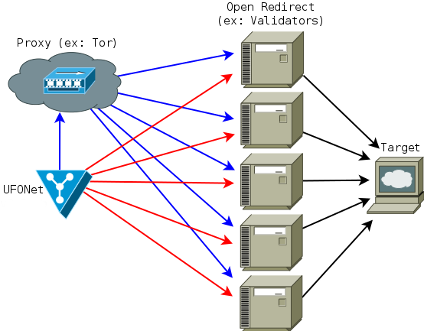
This schema shows you how the architecture of the requests are made when performing
a simple HTTP/WebAbuse DDoS attack.
- Is UFONet a "strong" botnet?
Well!. It depends on how you understand a botnet as "strong". If you understand it as;
* 'privacy'; UFONet is the best -ninja- DDoS/DoS tool...
* 'traffic volume'; it depends on; 'zombies', bandwidth, target's conf, etc...
With UFONet it's not about having a lot of 'zombies', it's more about those you have
work properly. If they are nice, you can 'defeat' a 'small' webserver just with
a 'couple of dozens'.
Or for example, in a scenario in which a target is using a VPS service with some limited
bandwidth rate (ex: 1GB/month) for the attacker is just a matter of time to run the tool
and wait until traffic (noise) reaches the maximum limit that closes the service.
Commonly people understand a botnet as an individual tool but UFONet is also a P2P/darknet,
that can be used to connect others machines and to run complex schemas involving other people
working cooperatively: sharing 'zombies', reporting statistics (with rankings, clans)...
Therefore, UFONet can also be defined fundamentally, as: a botnet of botnets, which is
obviously a harder and effective way to overwhelm an objective, than when a single person
tries it individually.
- What's the difference between: 'zombies', 'aliens', 'droids', 'ucavs'...?
* Zombie: HTTP GET 'Open Redirect' bot
ex: https://ZOMBIE.com/check?uri=$TARGET
* Droid: HTTP GET 'Open Redirect' bot with params
ex: https://ZOMBIE.COM/css-validator/validator?uri=$TARGET&profile=css3
* Alien: HTTP POST 'Open Redirect' bot
ex: https://ZOMBIE.com/analyze.html;$POST;url=$TARGET
* Drone: HTTP 'Web Abuse' bot
ex: https://www.isup.me/$TARGET
* X-RPC: XML-RPC Vulnerability
ex: https://ZOMBIE.COM/xmlrpc.php
- Is it possible to stress target's database using UFONet?
Yes, it is. For example, you can order to your 'zombies' to submit random valid requests
on a target's search input form. This floods database with queries.
ex(wordpress): ./ufonet -a 'http://TARGET.com' --db '?s='
- Can I directly attack an IP address?
Yes you can, as follows:
ex: ./ufonet -a 'http://IP'
- What kind of extra attacks does the tool have?
- LOIC: https://en.wikipedia.org/wiki/Low_Orbit_Ion_Cannon
- LORIS: https://en.wikipedia.org/wiki/Slowloris_(software)
- UFOSYN: https://en.wikipedia.org/wiki/SYN_flood
- FRAGGLE: https://en.wikipedia.org/wiki/Fraggle_attack
- UFORST: https://ddos-guard.net/en/terminology/attack_type/rst-or-fin-flood
- SPRAY: https://en.wikipedia.org/wiki/DRDOS
- SMURF: https://en.wikipedia.org/wiki/Smurf_attack
- XMAS: https://en.wikipedia.org/wiki/Christmas_tree_packet
- DROPER: https://en.wikipedia.org/wiki/IP_fragmentation_attack
- SNIPER: https://www.imperva.com/learn/application-security/snmp-reflection/
- TACHYON: https://www.us-cert.gov/ncas/alerts/TA13-088A
- PINGER: https://www.cloudflare.com/learning/ddos/ping-icmp-flood-ddos-attack/
- MONLIST: https://www.us-cert.gov/ncas/alerts/TA14-013A
- UFOACK: https://www.f5.com/services/resources/glossary/push-and-ack-flood
- OVERLAP: https://cyberhoot.com/cybrary/fragment-overlap-attack/
- UFOUDP: https://en.wikipedia.org/wiki/UDP_flood_attack
- NUKE: https://dl.packetstormsecurity.net/papers/general/tcp-starvation.pdf
How should a powerful attack that combines all the techniques (DDoS+DoS)?
sudo ./ufonet -a 'http://TARGET.com' --loic 1000 --loris 1000 --ufosyn 1000 /
--spray 1000 --smurf 1000 --xmas 1000 --nuke 1000 --tachyon 1000 --monlist 1001 /
--fraggle 1000 --sniper 1000 --ufoack 1000 --uforst 1000 --droper 1000 /
--overlap 1000 --pinger 1000 --ufoudp 1000 --threads 100
How can I start with UFONet; for example using GNU/Linux (ex: Kali)?
You can try to install automatically all required libs by using this command (as root):
% sudo python setup.py install
Which libs should I install?
python3-pycurl - Python bindings to libcurl (Python 3)
python3-geoip - Python3 bindings for the GeoIP IP-to-country resolver library
libgeoip-dev - Development files for the GeoIP library
libgeoip1 - non-DNS IP-to-country resolver library
python3-whois - Python module for retrieving WHOIS information - Python 3
python3-crypto - cryptographic algorithms and protocols for Python 3
python3-requests - elegant and simple HTTP library for Python3, built for human beings
python3-scapy - Packet crafting/sniffing/manipulation/visualization security tool
* Python: https://www.python.org/downloads/
* PyCurl: http://pycurl.sourceforge.net/
* GeoIP: https://pypi.python.org/pypi/GeoIP/
* Python-geoip: https://pypi.org/project/python-geoip/
* Pygeoip: https://pypi.org/project/pygeoip/
* Whois: https://pypi.python.org/pypi/whois
* PyCrypto: https://pypi.python.org/pypi/pycrypto
* PyRequests: https://pypi.python.org/pypi/requests
* Scapy-Python3: https://pypi.org/project/scapy-python3/
* Leaflet: http://leafletjs.com/ (provided)
Exists any HELP command?
You can read main HELP with:
./ufonet --help (or ufonet -h)
Also you can review some interesting (working) examples with:
./ufonet --examples
How can I start a Graphical User Interface (GUI)?
./ufonet --gui
What is a 'wormhole'?
It is an IRC gateway to Freenode where UFONet 'masters' can meet.
Is it possible to update the tool automatically?
Yes. But only if you have cloned UFONet from a Git repository.
* git clone http://code.03c8.net:3000/epsylon/ufonet
* git clone https://github.com/epsylon/ufonet
* ./ufonet --update
What is a 'blackhole'?
It is a P2P daemon to share 'zombies' with other UFONet 'masters'.
Where can I download more 'zombies'?
You should search for accessible 'blackholes'. Some of them are on the darknet...
By the way, there is a Community list of 'zombies' that you can download using:
./ufonet --download-zombies
Can I spread 'zombies' with a web-server?
Yes. You just need to create a 'blackhole' and share your IP with other UFONet 'masters'...
./ufonet --blackhole (daemonize it with: ./ufonet --blackhole &)
How can I know if my 'zombies' are working properly?
./ufonet -t 'botnet/zombies.txt'
Where can I report a bug?
You can report errors on: Github issues.
Also you can stay in touch reporting on my "mothership" (using BOARD provided by default).
If nobody gets back to you, then drop me an e-mail.
|


